-
Notifications
You must be signed in to change notification settings - Fork 694
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Alternative Endpoint #279
Comments
|
Hello There, Thanks for your this amazing find. I was having issue where Warp connected me to wrong data center. after change endpoint to above IP, it fixed the issue. |
|
Thanks! this allowed me to reduce my total latency by 400ms before it was 450 ish now its 50! |
|
Be careful as this is not the endpoint CF wants us consumers to connect to. According to their docs, this IP range is used for the Zero Trust client. Until now, WGCF only supports the consumer version of WARP and not the Zero Trust/Teams version. The Zero Trust WARP is more complex than that as it's integrated with authentications, session management, and more features used by companies to manage their employees. Thus, might introduce unknown errors at some point if we're using the Zero Trust endpoints. As for why it's not routing to the nearest PoP to you, CF already explained that it might be caused by many random factors such as:
Refer to FAQ for the details. Also, WARP+ is using Smart Routing, so it might re-route you to servers slightly further from you but have the best conditions compared to servers nearest to your country but they might be super busy at the time you're trying to connect. |
|
We did further research related to this issue and got some promising results. Underneath, it's using the It's also explained very well in the guide about the security & privacy considerations, to not cause a confusion. Technically speaking, if people want custom endpoints, they should make their own by hosting it in servers nearest to them. You <--> Your ISP (probably bad peering to cf) <--> WARP datacenterThe point of using a custom endpoint is to avoid bad peering quality between your ISP and Cloudflare. You <--> Your ISP <--> Your server/cloud (good peering to WARP and your ISP) <--> WARP datacenterThe one written by @DevinWinata is good enough, but defeats the purpose of using a custom endpoint if people's ISPs have bad peering with Cloudflare, so everyone is welcomed to test the theory in the guide. |
When using IP directly, your OS doesn't need to resolve the domain, so technically it should work unless your ISP prevents you from connecting to WARP endpoints. Resolving a domain to an IP requires a working DNS setup, the first thing you can do is to check your DNS setup and maybe use DoH to prevent DNS hijacking. Lastly, you can host your own wgcf relay, but it'll require you to get a cheap VPS for that. |
|
@peterweissbier
The things you want to check here are:
Point (2) is currently a known problem for users trying to connect to HKG colo not using the official apps. |
|
tested 1.1.1.1 warp app and it works fine - i was hoping that it would be able to import the generate config but i guess thats not an option there. i just found this qdm12/gluetun#1738 and i made it work, my fault was that i pointed the docker container to the file wg0.conf and it couldnt read the endpoint because it was not an IP, strangely enough i set an environment variable with the ip and the container will accept it just fine |
|
what to do if all alternative endpoints stop working? (blocked handshake) |
Host your own endpoint. |




Hello,



I just so happened to found this Cloudflare Zero Trust Docs (I haven't try dive deep into Zero Trust Docs) while googling about Cloudflare WARP Endpoints and IPs.
And I noticed on section WARP ingress IP, the IP is different from
engage.cloudflareclient.com (162.159.192.1)and it's IP range.IPv4 Range:
162.159.193.0/24IPv6 Range:
2606:4700:100::/48And I tried with IP
162.159.193.1and it worked.For me, the benefit of using IP
162.159.193.1is it routed to my nearest Cloudflare PoP rather than neighbouring country.Maybe you already routed to your nearest Cloudflare PoP using IP
162.159.192.1, then this is why I called it an Alternative Endpoint.Further "investigation" and maybe unrelated to the main point:

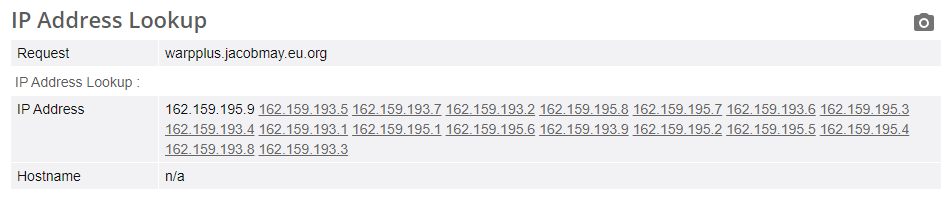
Reverse IP lookup (and IP lookup) reveals that maybe some person/organization have the same endpoint with multiple IPs and different subnet (probably Zero Trust customer or manually assign the IPs to a domain/subdomain).
Sorry if it's revealing private domains/subdomains.
This is just a "report" based on my own experience (and curiosity). If there's any duplicate/similar issue (or this is something that doesn't amuse you), my apology. Sorry for long post and thanks for reading.
The text was updated successfully, but these errors were encountered: