ok = ok && gguf_fread_str(file, &info->name, &offset); // [1] maybe read failed,then info->name = nullptr
ok = ok && gguf_fread_el (file, &info->n_dims, sizeof(info->n_dims), &offset);
ok = ok && (info->n_dims <= GGML_MAX_DIMS);
for (uint32_t j = 0; j < info->n_dims; ++j) {
ok = ok && gguf_fread_el(file, &info->ne[j], sizeof(info->ne[j]), &offset);
}
ok = ok && gguf_fread_el (file, &info->type, sizeof(info->type), &offset);
ok = ok && gguf_fread_el (file, &info->offset, sizeof(info->offset), &offset);
// TODO: return an error instead of crashing with GGML_ASSERT
gguf_tensor_info_sanitize(info);
// make sure there is no duplicated tensor names
for (uint64_t j = 0; j < i; ++j) {
if (strcmp(info->name.data, ctx->infos[j].name.data) == 0) { // [2] don't check wether data is nullptr
fprintf(stderr, "%s: duplicated tensor name %s\n", __func__, info->name.data);
ok = false;
}
}[1]: If gguf_fread_str fails to execute, name.data will not call GGML_CLLOC to allocate memory, so name->data will be nullptr.
[2]: don't check name.data whether is nullptr, so the strcmp will defer a null pointer then trigger segment fault.
static bool gguf_fread_str(FILE * file, struct gguf_str * p, size_t * offset) {
p->n = 0;
p->data = NULL;
bool ok = true;
ok = ok && gguf_fread_el(file, &p->n, sizeof(p->n), offset);
// early exit if string length is invalid, prevents from integer overflow
if (p->n == SIZE_MAX) { // exist before call GGML_CALLOC
fprintf(stderr, "%s: invalid string length (%" PRIu64 ")\n", __func__, p->n);
return false;
}
p->data = GGML_CALLOC(p->n + 1, 1);
ok = ok && gguf_fread_el(file, p->data, p->n, offset);
return ok;
}the resulte as follow:
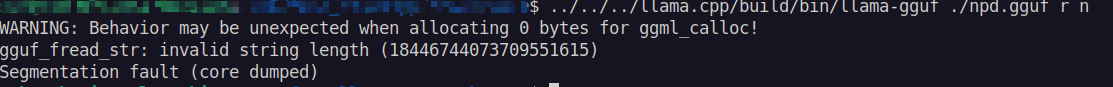
the poc of gguf file: https://github.com/Arashimu/images/raw/main/npd.gguf
[1]: If gguf_fread_str fails to execute,
name.datawill not call GGML_CLLOC to allocate memory, so name->data will be nullptr.[2]: don't check
name.datawhether is nullptr, so the strcmp will defer a null pointer then trigger segment fault.the resulte as follow:
the poc of gguf file: https://github.com/Arashimu/images/raw/main/npd.gguf