Goby Beta1.8.239
In this update
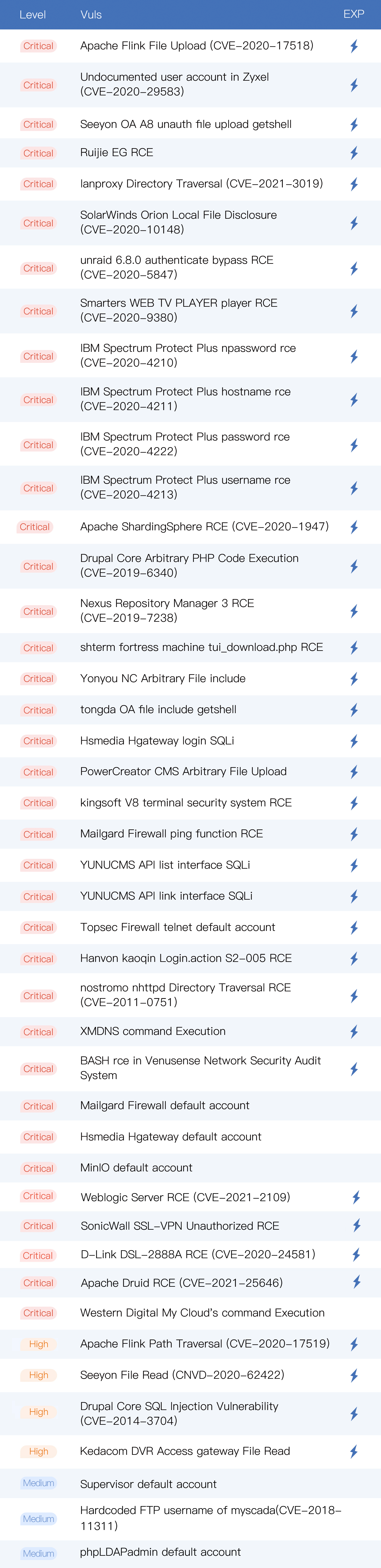
• A total of 44 new vulnerabilities: Weblogic Server RCE (CVE-2021-2109)、 Apache Flink Upload(CVE-2020-17518)、lanproxy Directory Traversal(CVE-2021-3019)、Ruijie EG RCE、Apache Druid RCE (CVE-2021-25646), etc;
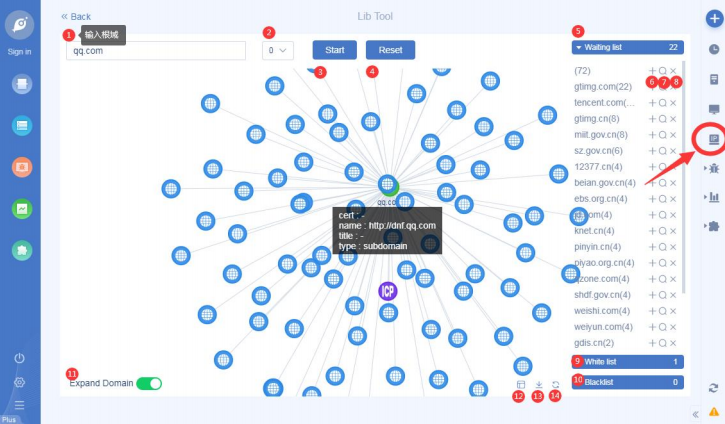
• Add IP library: flip chart combat! Through the root domain, quickly define a target network asset map;
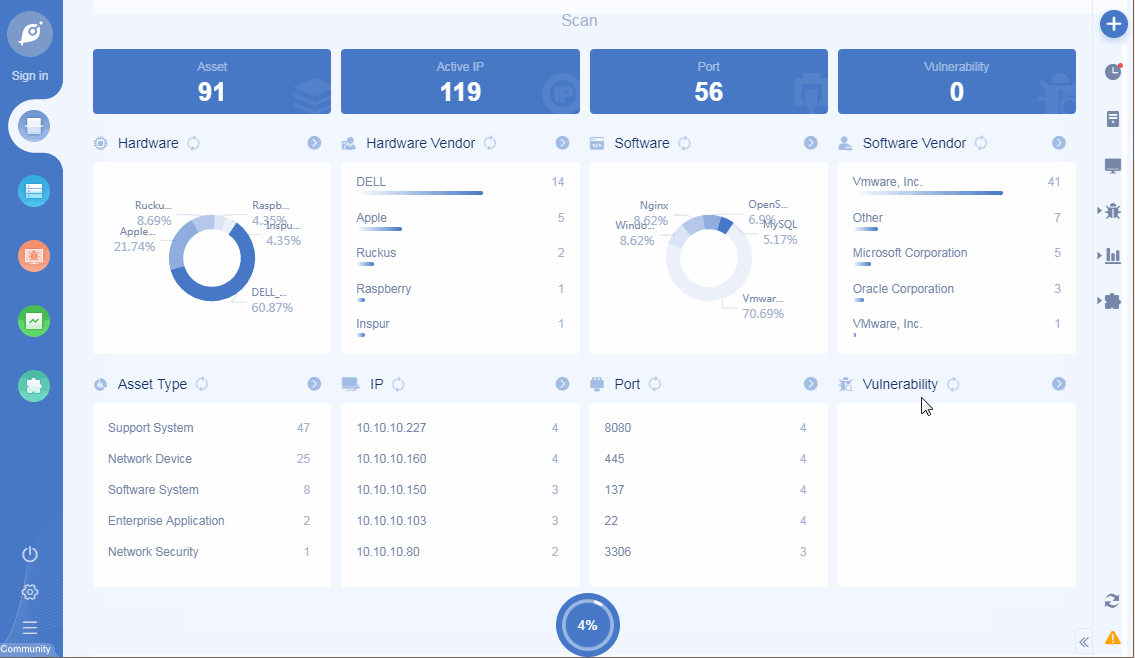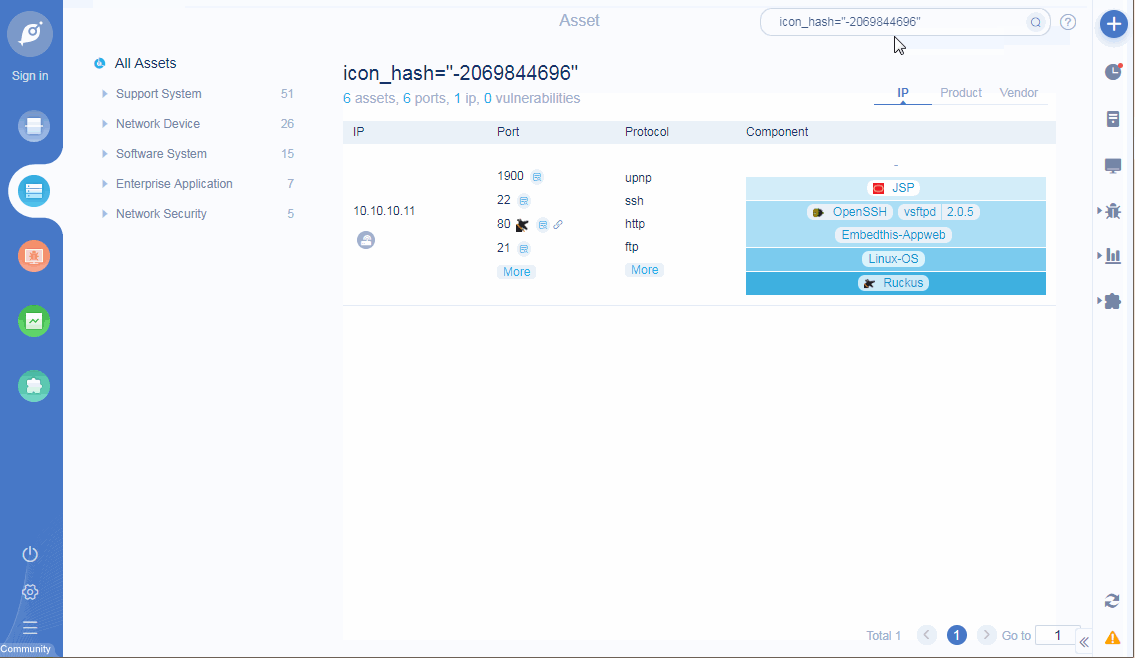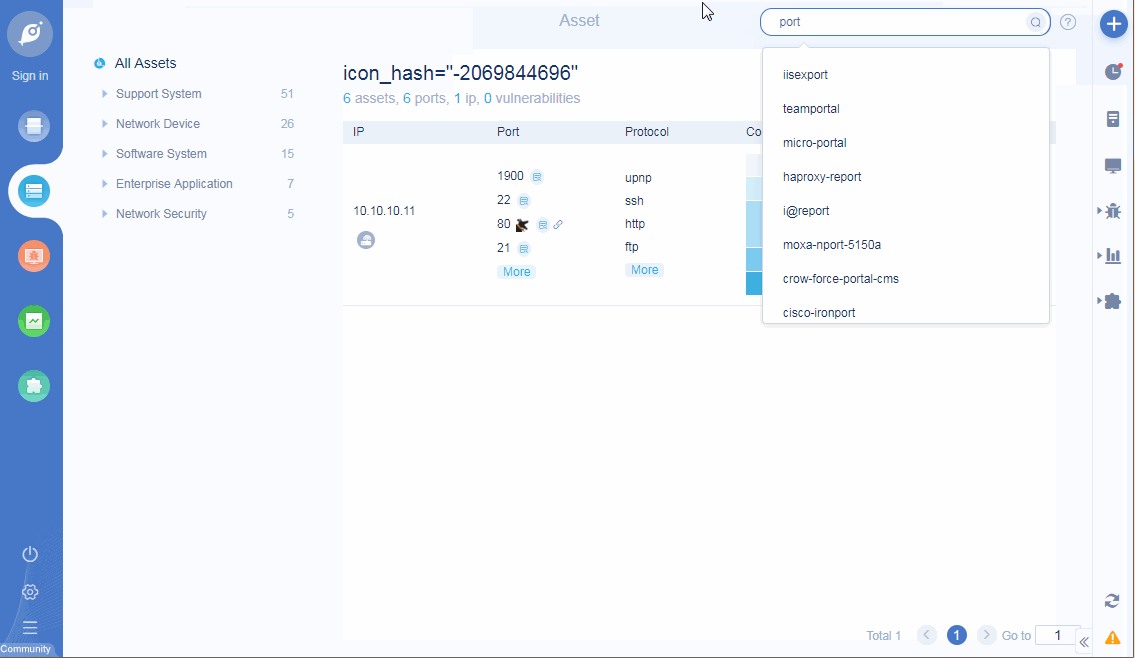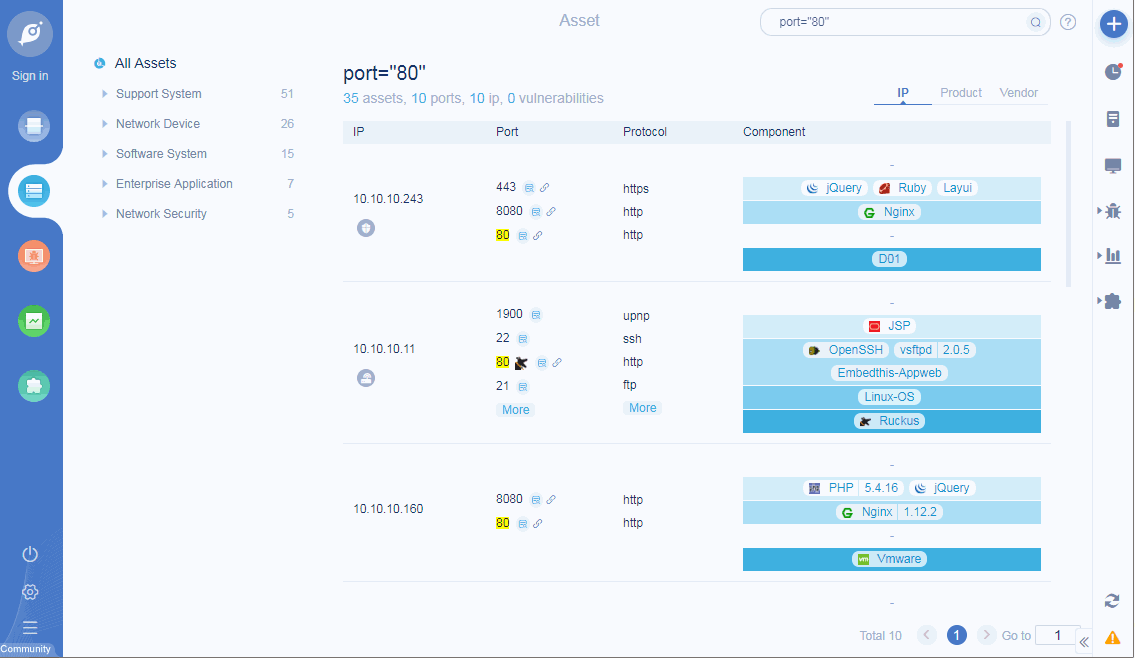
• Add ICON mapping function: support query rules to search current task assets, such as query ip, port, app, protocol, title, etc;
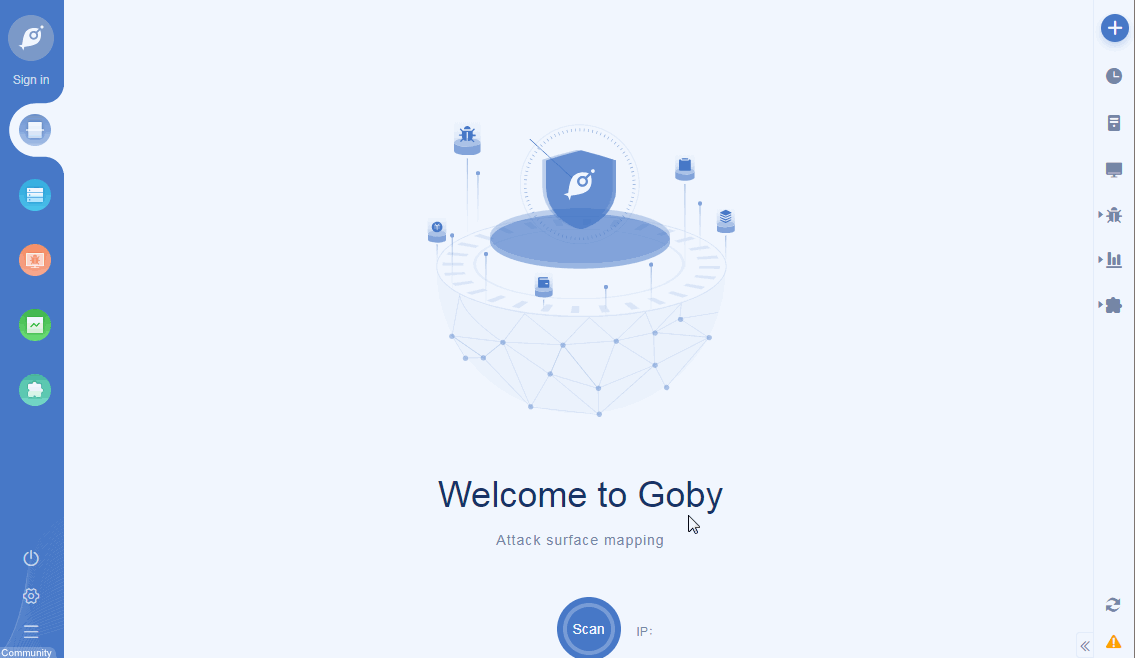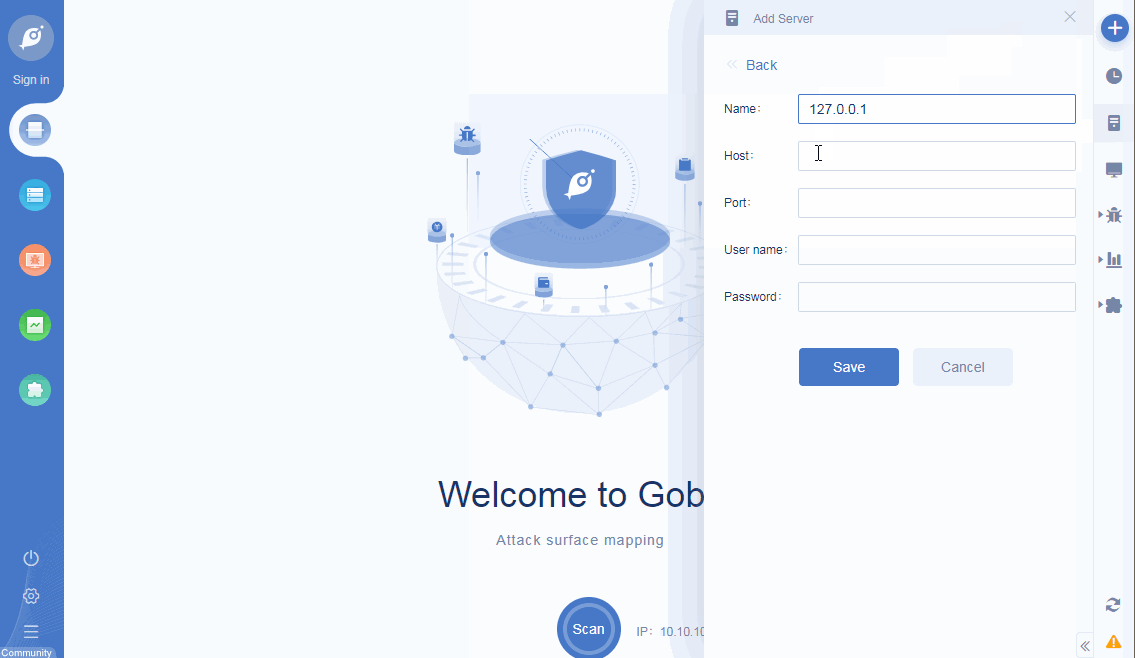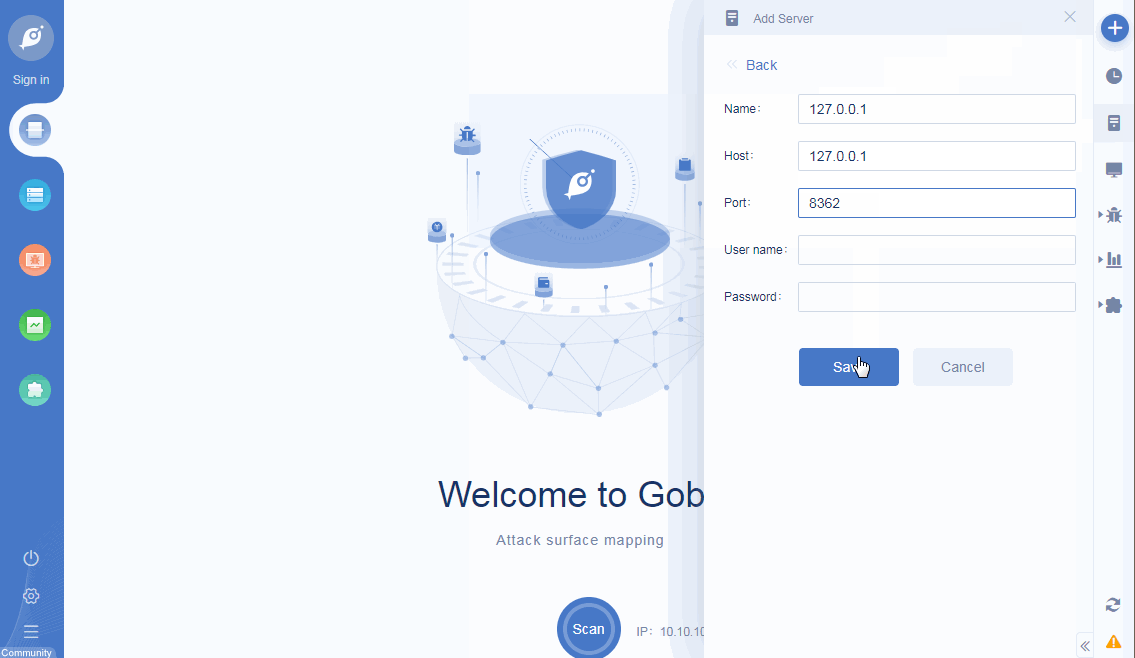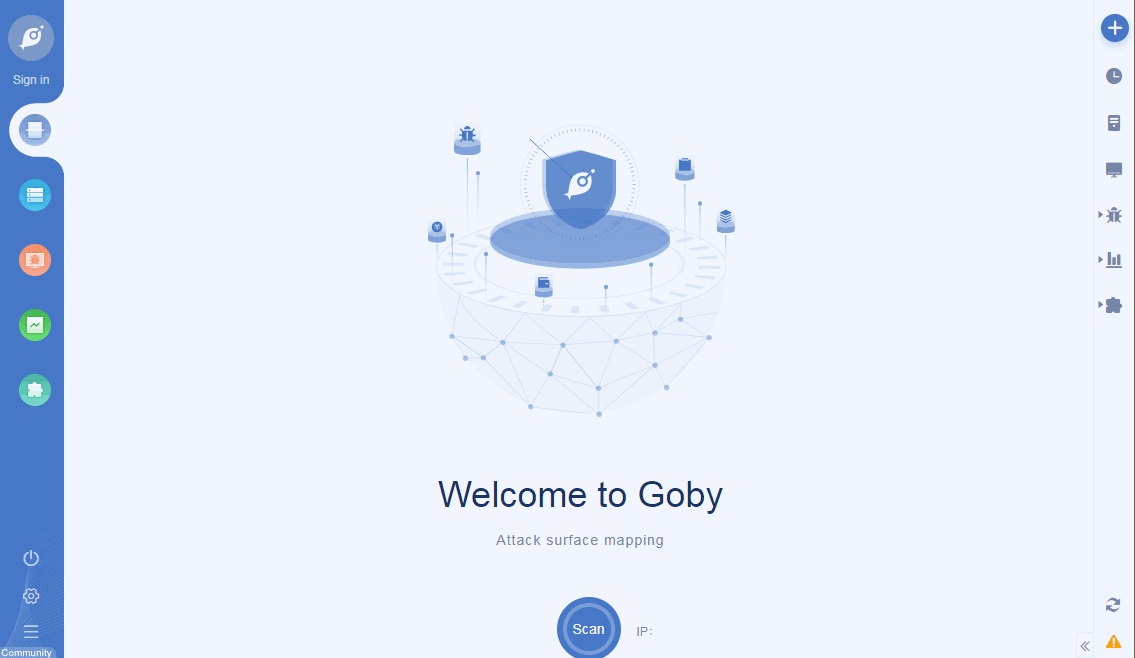
• New server management: support for adding multiple remote servers, and support for server management;
• Add support for windows 32-bit, mips and arm versions: currently limited to command line startup, the startup method is the same as windows 64-bit, run goby-cmd:
./goby-cmd -apiauth user: pass -mode api -bind 0.0 .0.0:8361
• New protocols: asterisk,barracuda-bcp,beacon ccnet,ceph,daap,firebird,nomachine-nx,remoting,rtmp,stun,svrloc,varnish-cli, etc;
• New extensions: weak password dictionary: DictionaryConfig, timing task function : Task Queue, etc;
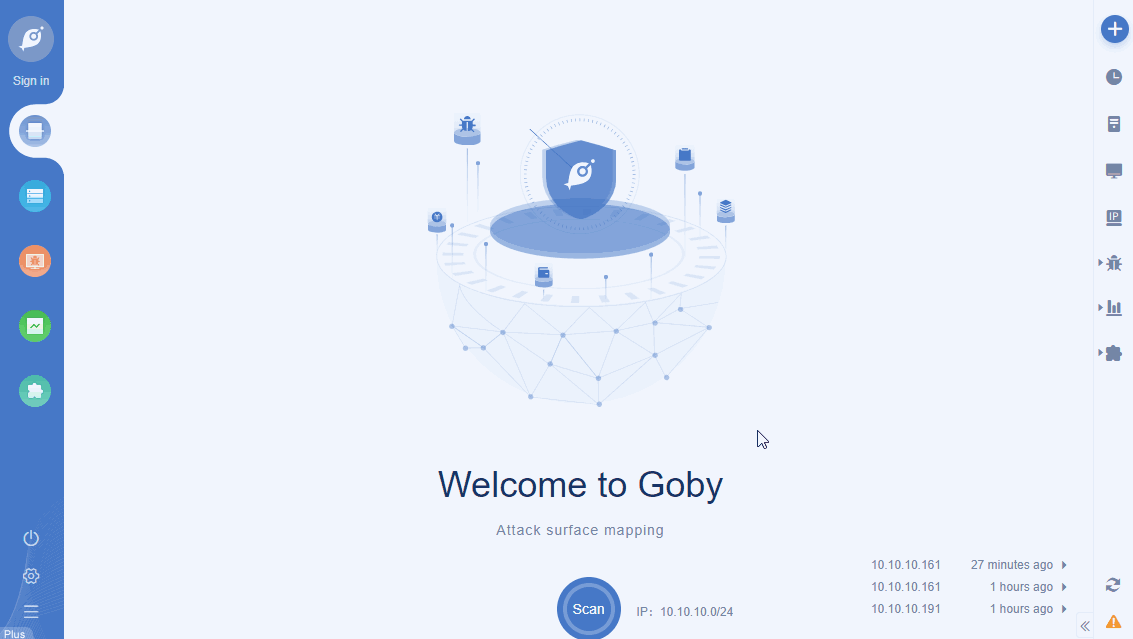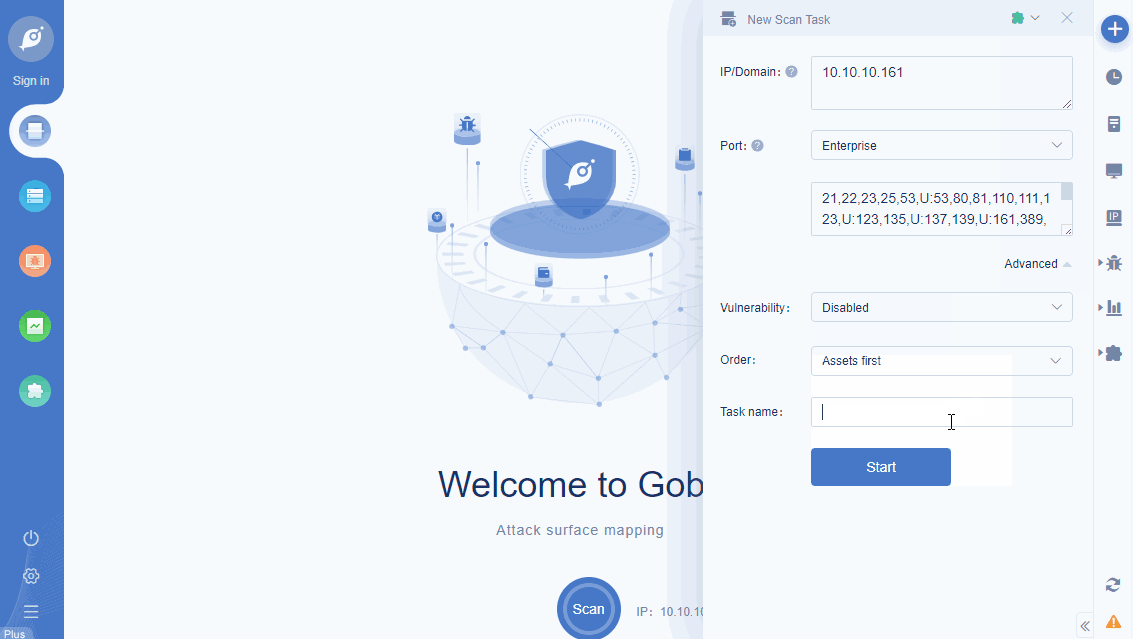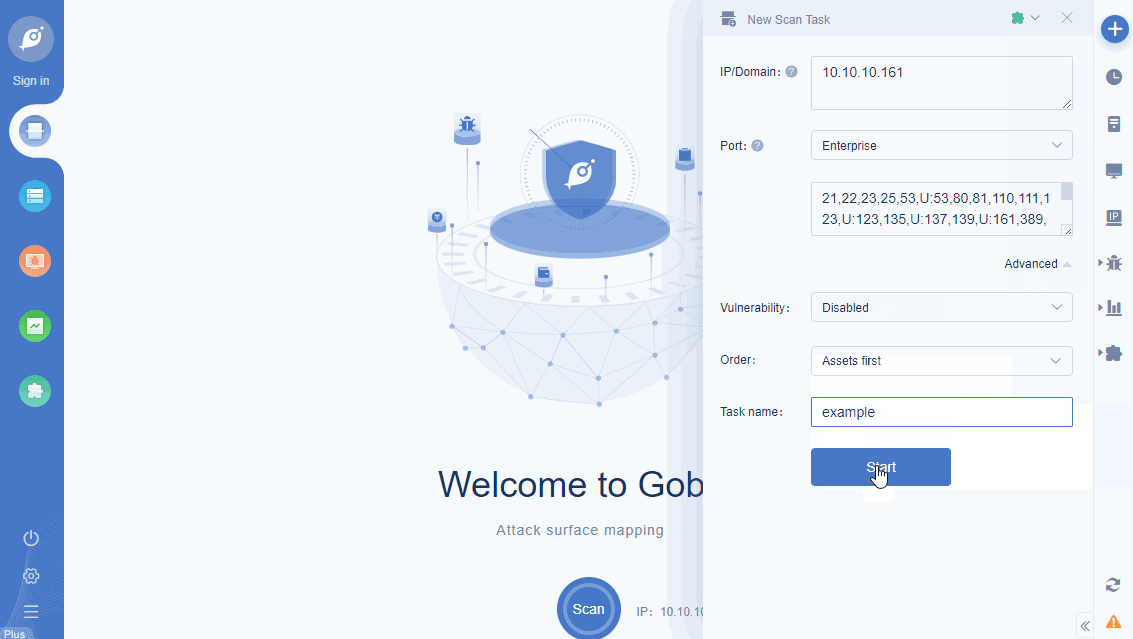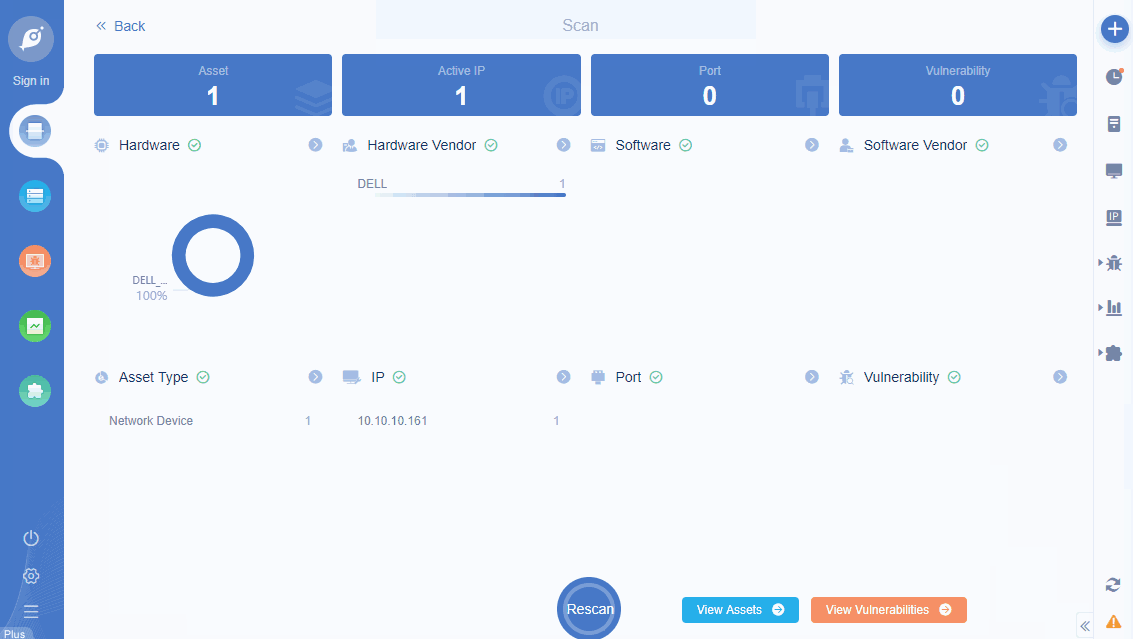
• Support specifying multiple poc for scanning;
• Fix online upgrade issues;
• Optimize the coding display of exploits;
• fix some mistake of pocs;
• Fix the issue of white screen caused by Chinese themes;
• Fix the problem that website screenshots cannot be displayed;
• Optimize partly hidden deep but frequently used functional interactions;
New vulnerabilities
Demos: https://github.com/gobysec/GobyVuls